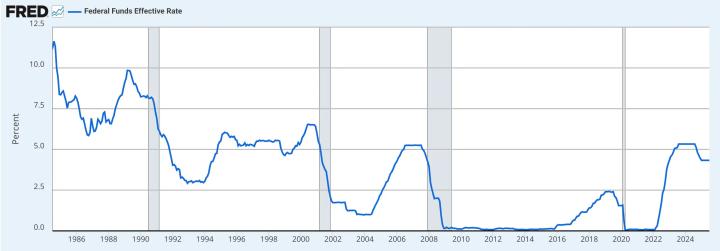
Here's the English translation:
A hacker once complained in a memo about "not understanding work requirements and not knowing what to do", with the corresponding solution being "work with dedication and double the effort"...
**Original Text:** An unnamed source recently compromised a DPRK IT worker device which provided insights into how a small team of five ITWs operated 30+ fake identities with government IDs and purchased Upwork/LinkedIn accounts to obtain developer jobs at projects.
**Author:** ZachXBT
**Translated by:** Azuma, Odaily
Editor's Note: North Korean hackers have long been a major threat to the cryptocurrency market. In previous years, victims and industry security professionals could only infer the behavior patterns of North Korean hackers through individual security incidents. However, yesterday, the well-known on-chain investigator ZachXBT cited an investigation by a white hat hacker who hacked into North Korean hackers in reverse, revealing their "work" methods from an active perspective for the first time, which may have certain positive significance for pre-emptive security deployment in industry projects.
An unnamed anonymous hacker recently infiltrated a North Korean IT worker's device, exposing the inner workings of a five-person technical team operating over 30 fake identities. **The team not only possessed government-issued fake identity documents but also infiltrated various development projects by purchasing Upwork/LinkedIn accounts.**
Investigators obtained their Google Drive data, Chrome browser configuration profiles, and device screenshots. The data showed that the team heavily relied on Google tools to coordinate work schedules, task assignments, and budget management, with all communications conducted in English.
A weekly report file from 2025 revealed the team's work mode and difficulties encountered, **such as a member complaining about "not understanding work requirements and not knowing what to do", with the corresponding solution column surprisingly stating "work with dedication and double the effort"...**
The expense details showed that **their expenditures included purchasing social security numbers (SSN), Upwork and LinkedIn account transactions, phone number rentals, AI service subscriptions, computer rentals, and VPN/proxy service procurement.**
One spreadsheet detailed the meeting schedule and script for the fake identity "Henry Zhang". The operational process showed that these North Korean IT workers would first purchase Upwork and LinkedIn accounts, rent computer equipment, and then complete outsourced work using the AnyDesk remote control tool.
One of their wallet addresses used for sending and receiving payments is: **0x78e1a4781d184e7ce6a124dd96e765e2bea96f2c**;
This address is closely linked on-chain to the $680,000 Favrr protocol attack in June 2025, which was later confirmed to involve North Korean IT workers with forged credentials as the CTO and other developers. Through this address, other North Korean IT personnel infiltrating projects were also identified.
The team's search records and browser history revealed additional key evidence.
Some might ask, "How can we confirm they are from North Korea?" **Besides all the fraudulent documents mentioned above, their search history showed frequent use of Google Translate, translating to Korean using Russian IPs.**
Currently, the main challenges for enterprises in preventing North Korean IT workers are concentrated in the following areas:
- Lack of Systematic Collaboration: Insufficient effective information sharing and cooperation mechanisms between platform service providers and private enterprises;
- Employer's Negligence: Hiring teams often adopt a defensive attitude after receiving risk warnings, and even refuse to cooperate with investigations;
- Numerical Advantage Impact: Although their technical methods are not complex, they continue to penetrate the global employment market by leveraging a massive base of job seekers;
- Fund Conversion Channels: Payment platforms like Payoneer are frequently used to convert legal currency income from development work into cryptocurrencies;
I have introduced the indicators to be noted multiple times before. Those interested can review my historical tweets, and I will not repeat them here.
Disclaimer: As a blockchain information platform, the articles published on this site represent only the personal views of the authors and guests, and are unrelated to Web3Caff's stance. The information in the articles is for reference only and does not constitute any investment advice or offer. Please comply with the relevant laws and regulations of your country or region.